Map a network drive via group policy is a much easier and faster process than manually or logon scripts. user does not have to wait for the logon script to load or if the network path changes it automatically updates. It makes admin and user’s life much better and makes changes to the network without having to update each user. It should plan out the process, users, or groups it’s going to apply this network drive.
This is my process for this post
- File server: FileServ1
- Share Name: Accounting
- Drive Letter: S
- Group that’s applying to: Accounting
- how-to-delete-policy
Create a new GPO
Start>Windows Administrative Tools>Group Policy Management
or from Server Manager: Tools>Group Policy Management
Right-click on your OU (Organization Unit) where you want to create and link your Group Policy
Select Create a GPO in this domain, and Link it here …
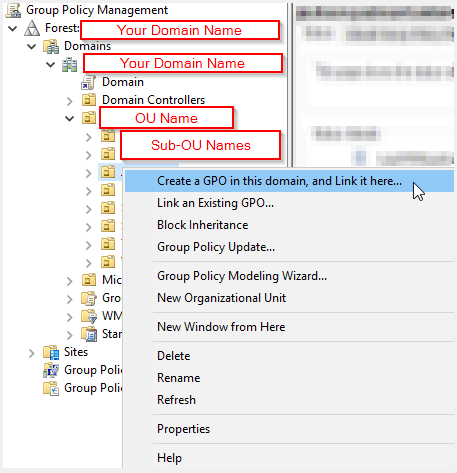
You will see New GPO, name it whatever you want, something that makes sense, I am going to call it Accounting Network Drive
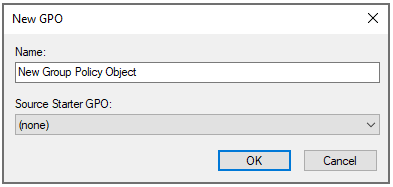
Configure GPO
Right-click on the Group Policy Object and select Edit
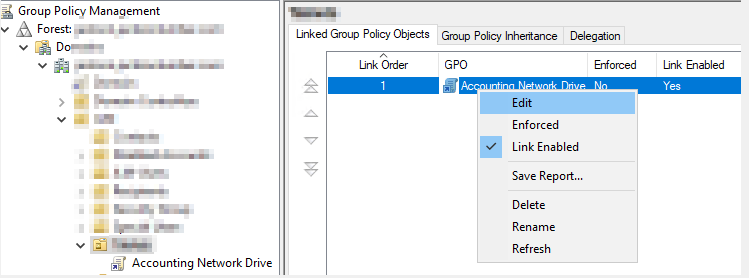
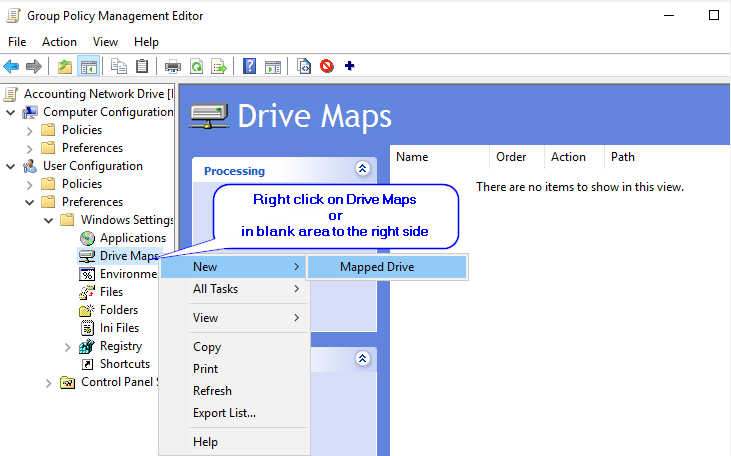
Expand User Configuration>Preferences>Windows Settings
Then right-click on Drive Maps and select New>Mapped Drive
Filling the details
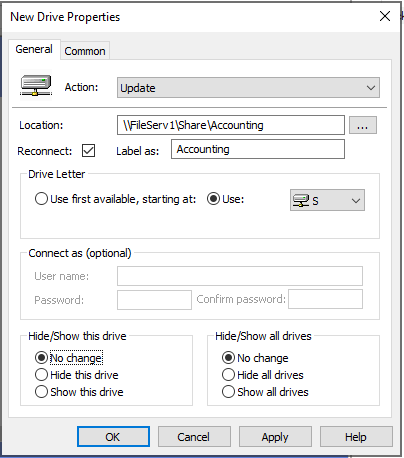
You can see there are many options to select from
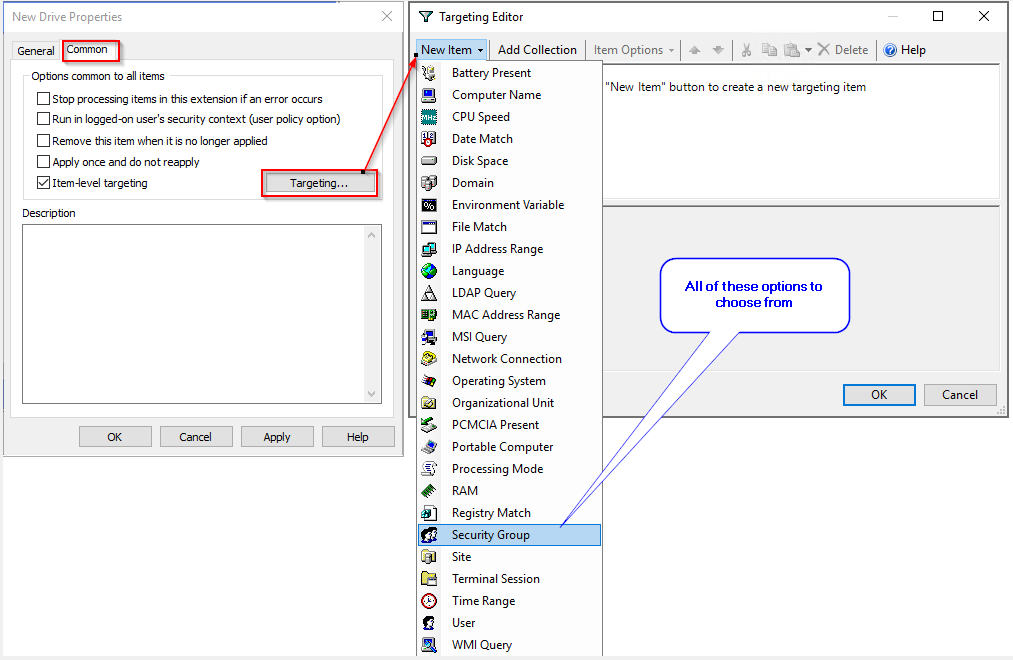
Based on select above you will see other options
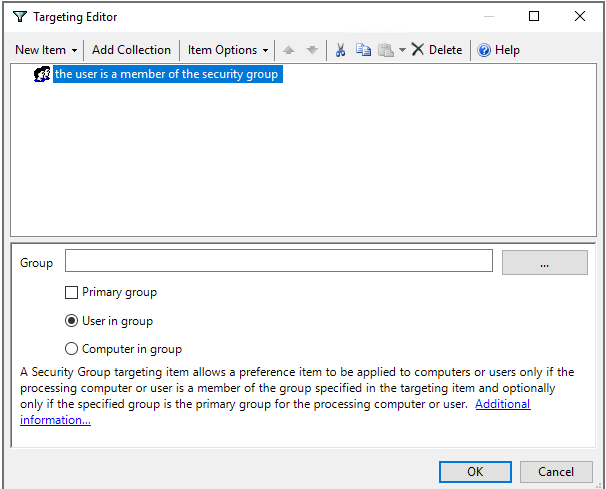
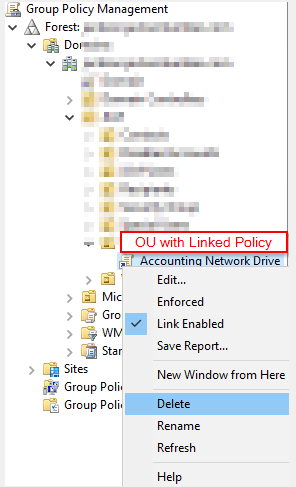
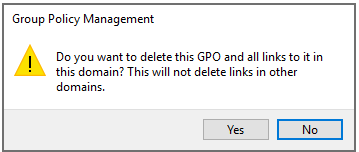
How to Delete policy
First unlink from OU that’s linked
Then Delete from Group Policy Objects:
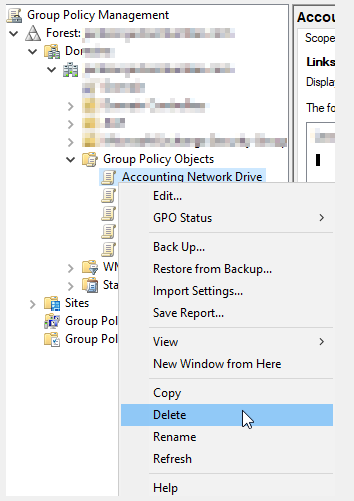
If you try to delete while still linked GPO, you will get this message, which also works fine too
That’s it, hope this help others