Here is how to free up space in the boot partition in Ubuntu, which may cause issues when trying to update or install a new application. Make sure you have a good backup and be careful running some commands, just double check typo before executing it.
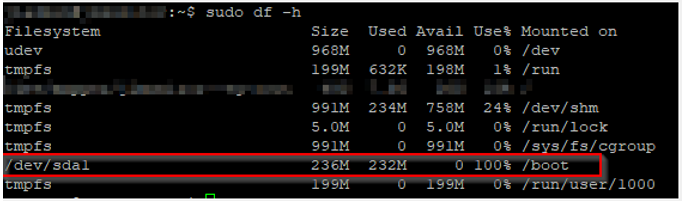
To see If you are running out of boot partition space, run the following command:
command: sudo df -h
You will see how much space is in use, in this screenshot, its /boot is 100% used
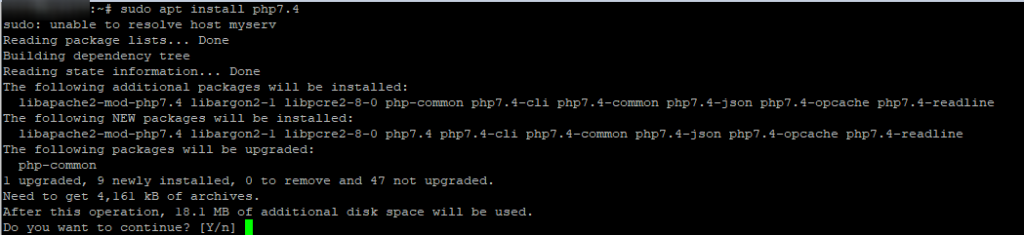
You can try the following command which may clean automatically for you some unused packages.
command: sudo apt autoremove
If the above command gives you an error, then continue do following steps
find your currently active boot image by running the following command:
Command: sudo uname -r
Output may look something like this: 4.15.0-143-generic
To list all images except for active:
Command: sudo dpkg –list ‘linux-image*’|awk ‘{ if ($1==”ii”) print $2}’|grep -v `uname -r`
Output:
linux-image-4.15.0-151-generic
linux-image-4.15.0-156-generic
linux-image-4.15.0-158-generic
To list of images:
sudo dpkg -l | grep linux-image
To remove unused images:
The numbers are based on the output command above, so if your version numbers are different, make sure you change them to match your output.
Command: sudo rm -rf /boot/*-4.15.0-{151,156,158}-*
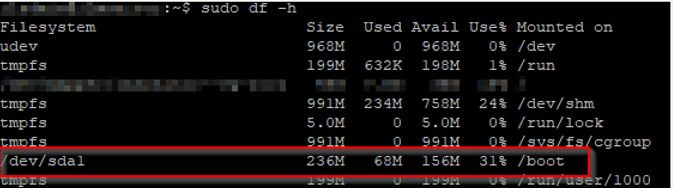
If you run df -h command to see how much space is in use, you will it went down from 100% to 31%:
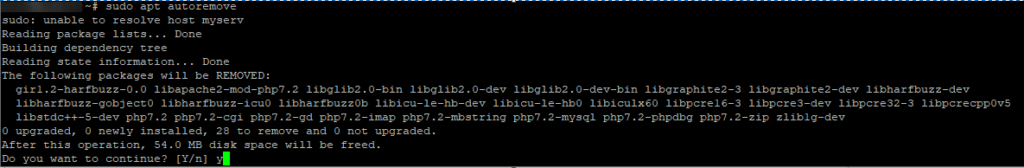
Now that you have some free space, let’s do some clean-up. If you try to clean up using apt autoremove, you may still get errors like these:
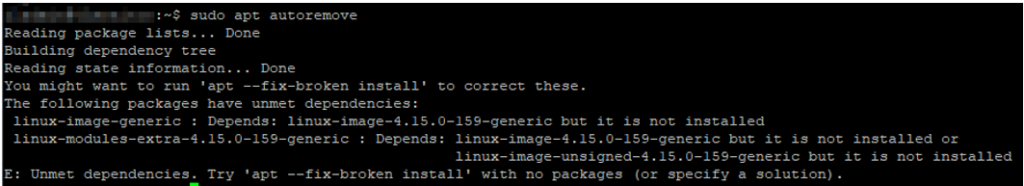
To Fix broken packages
You will need to fix the broken packages before you can do any other clean up, run the following command:
Command: sudo apt –fix-broken install
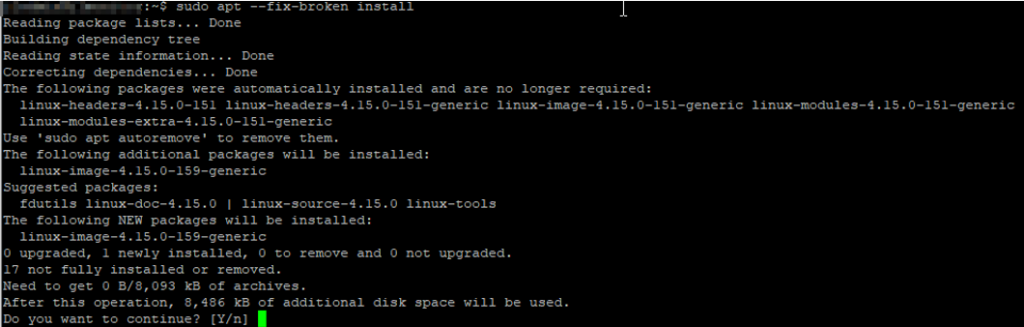
Now that broken packages are fixed, then re-run the autoremove command you will be able to free up disk space:
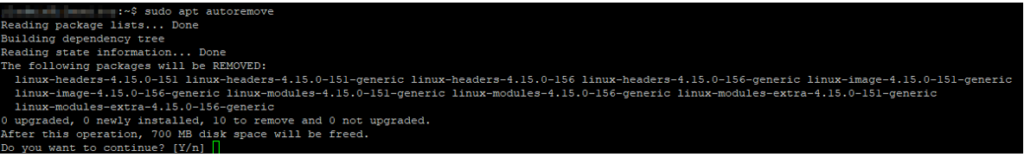
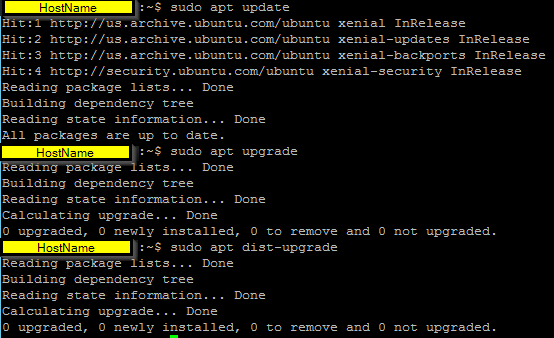
Update your system
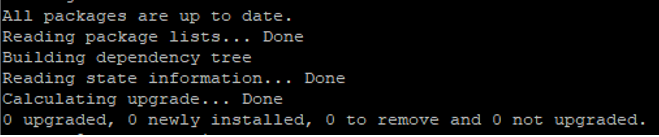
Then re-check for any updates and install it to secure your system:
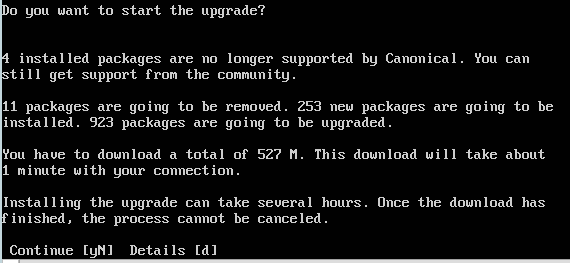
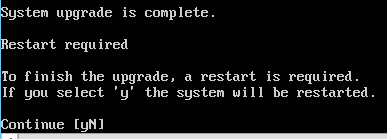
Command: sudo apt update && sudo apt upgrade
You want to see: All packages are up to date
That’s it, hope this helped you out